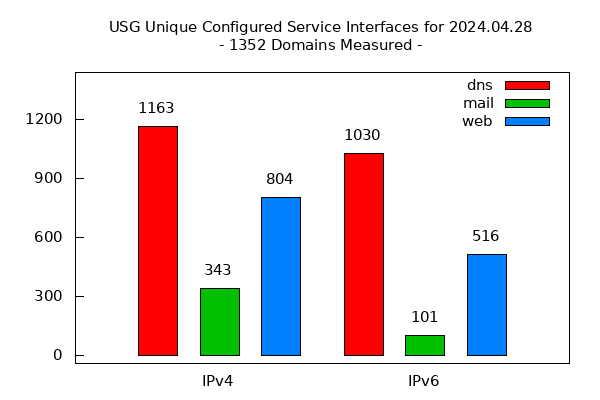
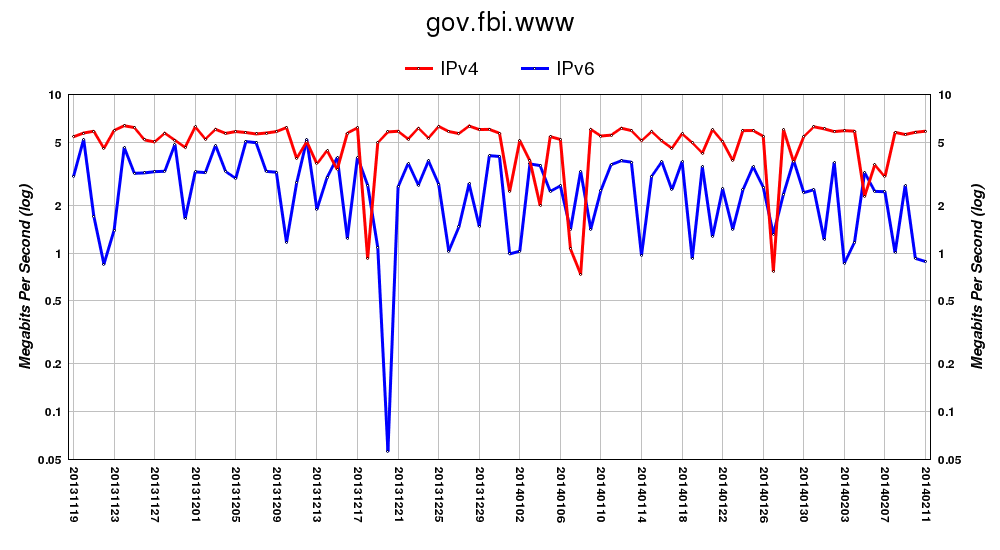
Note 1, this tool is unrelated to the USGv6 Profile and the USGv6 Testing Program. That is, no attempt is made to assess if the services monitored are running over IPv6 stacks that are compliant with the USGv6 Profile. The USGv6 Program is focused on acquisition and makes no recommendations about deployment scenarios. This tool on the other hand, only focuses on deployment issues.
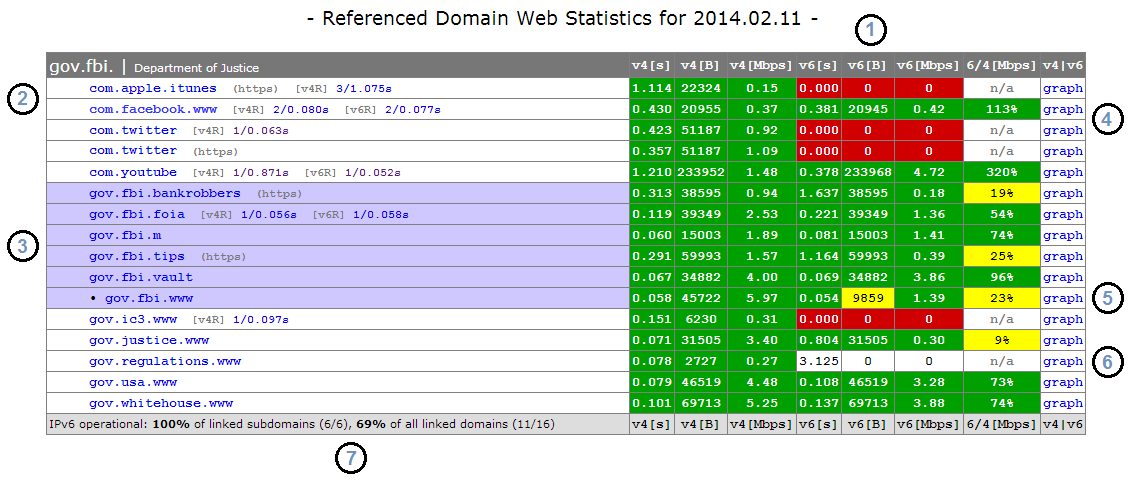
For each monitored domain and service we report the estimated number of IPv4 interfaces for that service, followed by an estimate of the number of those interfaces that (a) have an IPv6 address assigned, (b) of those, the number of interfaces whose IPv6 addresses are reachable (simply a 'ping' test, which is [understandably] frequently blocked - no color designations are made here) to our monitor, and finally, (c) the number of those interfaces actually running the service over IPv6 (e.g., answering DNS queries). Finally we include a heuristic indication of whether the service in question seems to be operating within the domain in question or provided elsewhere. The result is an output as follows:
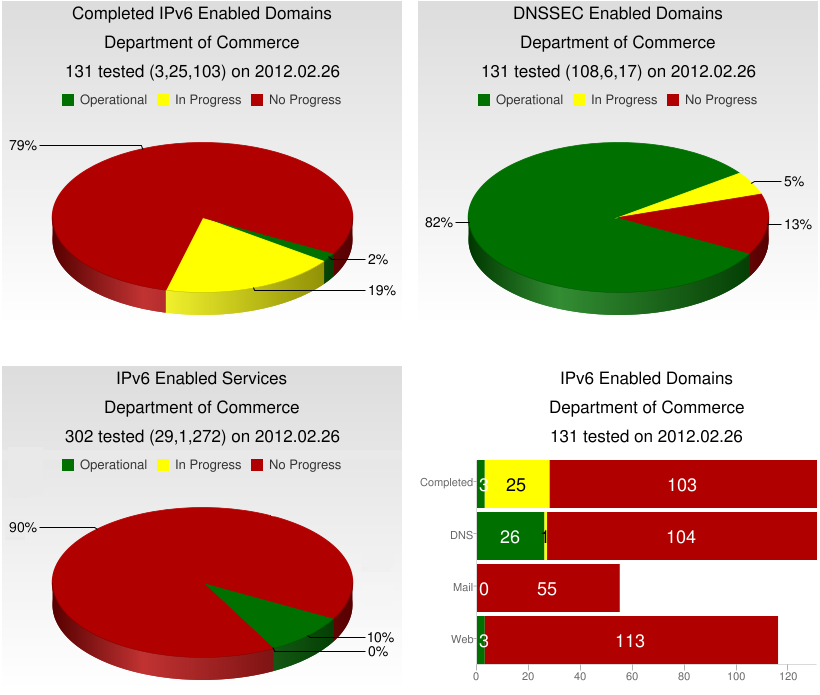
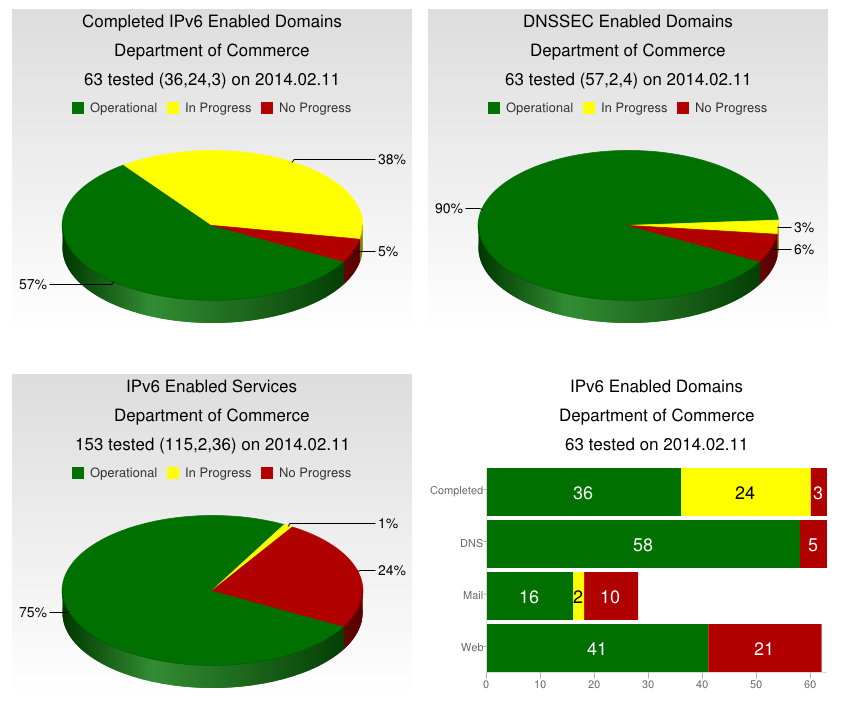
To conclude the data presentation, colors are added to the table to enhance readability. A red field indicates there is no server IP assignment in the DNS. A yellow field indicates assignments are present, may or may not be reachable, but are not operational. A green field indicates the domain has at least one fully ipv6 operational address. Gray is used to indicate when a service is intentionally not assigned. Applying all of these concepts the final table will look as follows:
The four states exist in five combinations of: